3-29-2015
One of the most important IT control areas to consider for any small, medium or large-scale organization is logical access to resources such as applications and databases. Logical access is the process by which a user or object is identified, authenticated and/or authorized to an application, system, database or another object[1]. Every organization must implement logical access in order to protect valuable data and resources, both internally and externally. Logical access to information prevents this data from being accessed by employees or external threats that might present a risk to the organization. This also ensures that the right resources are being accessed on a need-to-know basis, based on each individual’s role within the organization.
If an organization chooses to ignore implementing logical access controls, it runs the risk of losing proprietary data to the outside world, which could pose a threat to the organization. If you run a search on logical access breaches you will find thousands of recent examples of data that was extracted for malicious purposes by both employees of organizations and outside threats such as hacking groups. The following three steps will enable an organization to implement logical access and provide a basic framework to protecting its data.
Step 1: Identify gaps and risks regarding logical access
The first step must be to assess what types of controls are in place currently to protect organizational data, “what do we currently have”. From there, an evaluation must be directed to find out what types of controls are missing, “what do we need”. In regards to the missing controls, calculating the risk, impact and likelihood is a necessary part of this evaluation. Other criteria to consider are:
- Documenting a system inventory of all applications, databases, interfaces and systems within your organization.
- Excessive Privilege: What does each employee have access to? Are controls in place to ensure each employee has access to only what he or she needs to perform daily job duties? An example of excessive privilege would be if Sandra in Accounting had full access to the Human Resources system.
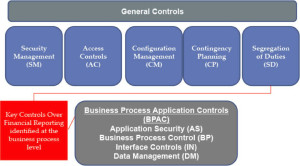
- Are the Access Control policy and procedures built off of a framework? Examples of frameworks are COSO, COBIT and NIST.
Step 2: Develop access control policy and procedures
The second step must be to develop an access control policy and procedures that adhere to the new policy. The policy will dictate an organizational wide process to implementing the access controls. Although developing a new policy can be a daunting task, the NIST, COSO and COBIT frameworks offer a great deal of information including templates to developing your access control policy and procedures.
Once the policy and procedures are outlined and developed, they must be updated, revised and tested for any errors and omissions. All members of the organization must be involved in the development process to make sure that every department’s opinions and concerns are taken into consideration. For example, if you leave the development of the policy strictly to IT management, it might restrict too much access for anyone to conduct his or her daily duties. On the other hand, if HR develops the policy, it might be too lenient and not address any threats appropriately.
Step 3: Continuously monitor and update with any changes
As the world evolves, so will its existing threats, vulnerabilities and risks. Therefore, the last step of improving logical access consists of continually monitoring and updating the implemented policy and procedures as necessary. In addition, reviews of access controls should be conducted on a periodic basis as deemed necessary by the organizational, or as dictated by policy. This will ensure that all changes to the organization are considered and implemented into the access policy.
To close, access controls are necessary and an integral part of any organization, no matter what its size. Every organization must implement logical access in order to protect its data and resources from internal and external threats. The steps above are general and will help you get started. Each organization will have to tailor these steps as necessary. Each organization will also add or remove steps that do not present a risk at the time. In addition, implementing these steps will not guarantee that you will pass an IT audit. For assistance in understanding the requirements of an IT Audit or for help getting optimal results, please contact us. As always, if you or someone you know needs assistance in understanding or implementing a new access control policy, please do not hesitate to contact us at [email protected].
————————
[1] This is not to be confused with physical access, which can also accomplish the same means, however not through the use of software alone.